#Splunk Partners
Explore tagged Tumblr posts
Text
Security and Compliance in the Cloud: Proactive Strategies for Risk Mitigation
As organizations shift their workloads to the cloud, ensuring robust security and compliance has become a top priority. With evolving cyber threats and stringent compliance requirements, businesses must adopt proactive strategies to safeguard data, applications, and infrastructure.
In this blog, we explore key security risks in cloud computing, the importance of compliance, and best practices to mitigate risks effectively.
Understanding Cloud Security Risks
While the cloud offers scalability and flexibility, it also introduces unique security challenges that businesses must address:
🔹 Data Breaches & Unauthorized Access
Weak authentication methods can expose sensitive data to cybercriminals.
Misconfigured cloud settings often lead to accidental data exposure.
🔹 Compliance Violations
Many industries require adherence to standards like GDPR, HIPAA, and ISO 27001.
Non-compliance can result in fines, legal consequences, and reputational damage.
🔹 Lack of Visibility & Control
Shadow IT (unauthorized cloud usage) increases security risks.
Multi-cloud environments can complicate security management.
🔹 DDoS and Insider Threats
Distributed Denial of Service (DDoS) attacks can disrupt cloud services.
Insider threats—whether malicious or accidental—pose significant risks to data integrity.
🚨 To counter these risks, businesses must adopt a proactive security and compliance strategy.
Proactive Strategies for Risk Mitigation
To ensure a secure and compliant cloud environment, organizations should implement the following best practices:
✅ 1. Implement a Zero Trust Security Model
🔒 “Never trust, always verify.”
Enforce multi-factor authentication (MFA) for all users.
Use role-based access control (RBAC) to limit privileges.
Monitor access logs to detect suspicious activity.
✅ 2. Encrypt Data at Rest and in Transit
🔑 Data encryption is critical for securing sensitive information.
Use AES-256 encryption for data stored in the cloud.
Ensure all communications use SSL/TLS encryption.
Regularly rotate encryption keys for enhanced security.
✅ 3. Automate Compliance Monitoring
📊 Continuous compliance tracking helps businesses avoid penalties.
Use compliance automation tools to check adherence to standards like SOC 2, PCI-DSS, and NIST.
Automate audits with cloud security posture management (CSPM) tools.
🛠 Recommended Tools: AWS Config, Microsoft Defender for Cloud, Prisma Cloud
✅ 4. Strengthen Cloud Monitoring and Threat Detection
🕵️ Real-time threat monitoring is essential to prevent cyberattacks.
Deploy SIEM (Security Information and Event Management) tools to analyze threats.
Use Intrusion Detection & Prevention Systems (IDPS) to block attacks.
Enable security logging to track abnormal user behavior.
🛠 Recommended Tools: Splunk, IBM QRadar, Google Chronicle
✅ 5. Regular Security Assessments and Penetration Testing
🔍 Continuous testing helps identify vulnerabilities before attackers do.
Perform automated vulnerability scanning across cloud workloads.
Conduct penetration tests to assess cloud security gaps.
Keep security patches updated to mitigate software vulnerabilities.
Ensuring Compliance in the Cloud
Compliance requirements vary based on industry regulations. Here’s how businesses can maintain compliance in the cloud:
📜 Common Cloud Compliance Frameworks
✔ GDPR (General Data Protection Regulation) – Protects personal data for EU residents. ✔ HIPAA (Health Insurance Portability and Accountability Act) – Secures healthcare information. ✔ SOC 2 (Service Organization Control 2) – Ensures cloud security best practices. ✔ ISO 27001 – International standard for cloud security governance.
🚀 Compliance Best Practices
✔ Keep detailed audit logs to track access and changes. ✔ Use automated compliance reporting tools. ✔ Partner with cloud service providers (CSPs) that meet compliance standards.
How Salzen Cloud Enhances Security and Compliance
At Salzen Cloud, we help businesses implement end-to-end security and compliance solutions to protect their cloud infrastructure. Our automated security frameworks ensure continuous compliance monitoring, threat detection, and risk mitigation.
🔹 Advanced encryption and identity management 🔹 Real-time security monitoring and incident response 🔹 Automated compliance tracking for regulatory frameworks
🚀 Want to secure your cloud infrastructure? Contact Salzen Cloud today!
0 notes
Text
DevOps Services and Solutions: Driving Efficiency and Innovation
In today's fast-paced digital world, businesses strive for agility, efficiency, and reliability in their software delivery processes. This is where DevOps Consulting Services and Solutions play a pivotal role.
DevOps integrates development and operations teams, fostering a culture of collaboration and automation. By implementing best practices, tools, and workflows, businesses can streamline their software development lifecycle and deliver high-quality applications faster.
Key Benefits of DevOps Services:
Accelerated Deployment: Automate processes to reduce time-to-market.
Enhanced Collaboration: Break down silos between teams for smoother workflows.
Improved Quality: Continuous testing and monitoring ensure reliable and secure applications.
Scalability: Easily adapt to business growth and technological changes.
DevOps Consulting Services and Solutions Include:
Assessment and Strategy: Evaluating current processes and designing a tailored DevOps roadmap.
CI/CD Implementation: Setting up Continuous Integration and Continuous Deployment pipelines for seamless updates.
Infrastructure Automation: Utilizing tools like Terraform or Ansible for efficient resource management.
Monitoring and Feedback: Integrating tools like Prometheus or Splunk for real-time insights and improvements.
By adopting DevOps, businesses can achieve operational efficiency, faster innovation, and enhanced customer satisfaction. Whether you're a startup or an enterprise, DevOps Consulting Services and Solutions can transform your IT landscape and position your business for long-term success.
Ready to embrace DevOps? Partner with Stigasoft today to streamline your operations and drive innovation! Contact us to get started.
0 notes
Text
Dell Trusted Device & SafeBIOS: Pillars Of Endpoint Security

The Trade Secret of Dell’s Reliable Devices. Have you ever wondered why it products are the safest business PCs on the market? Dell SafeBIOS and Dell Trusted Device (DTD) software are two special endpoint security features that are included with Dell Technologies business PCs.
Dell SafeBIOS: Protecting the Device at the Deepest Levels
With integrated firmware attack detection, Dell SafeBIOS is a set of features that reduces the possibility of BIOS and firmware manipulation. It includes partner technologies in addition to Dell’s exclusive intellectual property. It integrate these features to help make sure devices are safe at the BIOS level, which is often unprotected but is undoubtedly recognized to hackers as a place to take advantage of if it is weak. BIOS-level attacks have the potential to be very destructive and covert. Additionally, malware gains control of the PC and network access when it takes control of the BIOS.
Some of these features, such as BIOS Guard and Intel Boot Guard, are industry standards. The others, including Indicators of Attack, or IoA, which identifies potentially harmful changes to BIOS properties, are only offered by Dell. Image Capture for Forensic Analysis is another example of a feature offered by Dell that goes beyond the standard option of only switching back to the reliable BIOS. This feature may assist protect the device by capturing a snapshot of the faulty BIOS and making it accessible for forensic investigation. It enables security operations centers (SOCs) to examine the incident in order to assist stop similar assaults in the future.
The BIOS safeguards of Dell and it partner are robust on their own. However, because security is a team sport, Dell has teamed up with top partners to strengthen protection “below the OS,” which is where far too many assaults nowadays start.
Dell Trusted Device (DTD) Software: Maximizing Protections Through PC Telemetry
Dell tops the industry in BIOS safeguards, as shown by SafeBIOS IoA and Image Capture. But how can all that telemetry help you? DTD software is useful in this situation. Through endpoint telemetry communication between the device and a secure Dell cloud, DTD software optimizes SafeBIOS capabilities and offers special below-the-OS insights on security “health.”
The transmission of the data ensures that the BIOS is being measured. The IT administrator is alerted to potential manipulation if any feature reports suddenly change.
Dell Trusted Device program offers telemetry to activate many Dell SafeBIOS functions, including BIOS Verification and IoA, which identify BIOS firmware manipulation. Additionally, it offers to Health Score, a feature that combines multiple indicators into a single, easily readable security score, and Intel ME (Management Engine) Verification, which checks the integrity of highly privileged ME firmware on the platform by comparing it with previously measured hashes (stored off-host).
The Windows Event Viewer, which is a record of system and application messages, including warnings, information messages, and problems, provides the administrator with alerts. It’s a helpful tool for problem-solving.
How DTD Software Improves Security and Manageability
It wide partner connections allow Dell Trusted Device software to function in many of the clients’ settings, which is one of its main benefits. Actually, only Dell enhances fleet-wide security by combining device telemetry with cutting-edge software. True hardware-assisted security is the outcome of this.
DTD software can provide telemetry to SIEMs like Splunk, endpoint management like Microsoft Intune and Carbon Black Cloud, and third-party security programs like VMware Carbon Black and CrowdStrike Falcon.
These connections not only help you maximize your software investments, but they also enhance threat detection and response by providing a fresh set of device-level data. To keep releasing updates to Dell Trusted Device software that allow for more integration options since the understand how much it clients enjoy being able to see (for example, security warnings) in the settings of their choice.
For instance, it increased the number of important feature integrations in the Intune environment this autumn. With more features to be included in further DTD versions, Intune administrators may now access more information from BIOS Verification, Intel ME Firmware Verification, and Secured Component Verification (also known as SCV, a component integrity check exclusive to Dell).
Take Advantage of Dell’s Built-in Security
These safeguards, which are all part of the device’s price, are probably already advantageous to you if you own or oversee Dell business PCs.
With the built-in capabilities of Dell SafeBIOS, all Dell business PCs instantly increase the security of any fleet.
Your PC came with Dell Trusted Device software if you bought a commercial device after August 2023. Nous now ship with the “standard” image and pre-install DTD software at the plants. To download and install the program on older devices or for companies who would rather use their own picture, go this link.
Read more on Govindhtech.com
#DellTrustedDevice#DTD#SafeBIOS#Security#PCs#DellSafeBIOS#BIOS#safeguards#DTDsoftware#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
1 note
·
View note
Text
Conquer Your Data Challenges with Web Age Solutions' Data Engineering Courses
Organizations are constantly bombarded with information. The ability to effectively collect, store, transform, and analyze this information is crucial for gaining valuable insights and making informed decisions. This is where data engineering comes in. Data engineers are the architects of the data pipelines that power these insights.
Web Age Solutions empowers you to build a skilled data engineering team with our comprehensive suite of data engineering courses. Led by industry experts, our courses provide a blend of theoretical knowledge and practical application, equipping you with the skills to tackle critical data challenges head-on.
What You'll Gain from Our Data Engineering Courses:
Master Data Wrangling with Python: The "Data Engineering with Python" course delves into the practical application of Python, a widely used programming language in data engineering. You'll gain proficiency in popular Python libraries like NumPy, pandas, and Matplotlib, enabling you to manipulate, analyze, and visualize data effectively.
Bridge the Gap for Data-Driven Leaders: The "Data Engineering for Managers" course is designed for business leaders who want to understand the fundamentals of data engineering and its role in driving business outcomes. This course equips you to make informed decisions about data infrastructure and effectively communicate with your data engineering team.
Harness the Power of Operational Data Analytics: "Operational Data Analytics with Splunk" introduces you to the Splunk platform, a powerful tool for analyzing machine-generated data. Through hands-on exercises, you'll learn to onboard and forward data, monitor systems in real-time, and create informative data visualizations.
Embrace Cloud-Based Data Processing: "Cloud Data Engineering with NiFi on AWS or GCP" equips you with the skills to leverage Apache NiFi, a visual programming tool, for data processing on cloud platforms like AWS and GCP. This course blends theoretical concepts with practical guidance to help you automate data movement and transformation within cloud environments.
Build a Solid Foundation in Data Engineering: "Data Engineering, ETL and DataOps" provides a comprehensive introduction to core data engineering principles. You'll gain hands-on experience with ETL (Extract, Transform, Load) processes, data manipulation with pandas, data visualization using Python, and essential data operations (DataOps) practices. Additionally, the course covers Apache Spark and Spark SQL, further equipping you for success in data engineering and data analytics roles.
Investing in Your Data Engineering Skills:
By empowering your team with data engineering expertise, you unlock a wealth of benefits for your organization. Data engineers can help you:
Optimize Risk and Performance: Analyze data to identify potential risks and opportunities, allowing for proactive decision-making.
Enhance Data Quality: Implement processes and tools to ensure data accuracy and consistency, leading to reliable insights.
Forecast with Precision: Leverage data to predict future trends and customer behavior, enabling informed business strategies.
Streamline Business Processes: Automate data-driven workflows, improving efficiency and productivity across your organization.
Web Age Solutions: Your Partner in Data Engineering Education
Our data engineering courses are designed to cater to a wide range of learners, from beginners seeking a foundational understanding to experienced professionals looking to refine their skillset. We offer flexible delivery options, including on-site and instructor-led virtual classes, to accommodate your team's learning preferences.
Ready to unlock the power of your data? Browse our complete course catalog or contact Web Age Solutions today to discuss your data engineering training needs. With expert-led instruction and a practical approach, we will equip your team with the skills to transform your data into actionable insights.
For more information visit: https://www.webagesolutions.com/courses/data-engineering-training
0 notes
Text

Partners See More Opportunities, Few Downsides In Splunk-Cisco Integration http://dlvr.it/T8Tv2G
0 notes
Text
Anvennsa-AI
Anvenssa.AI is a privately held company headquartered in the India, It has a sizable partner network that gives it a broad geographic presence.
We’re here to deliver you an amazing experience, fueled by the passion to change the day-in-the-life of your employees and customers. Our goal is to help users with greater self-service by automating common to complex actions and tasks. This enables users to focus on high-value work, while those requesting help can resolve their issues with self-service resolutions. We hail from companies such as ServiceNow, Splunk, VMware, Google, Microsoft, SAP, and LinkedIn. We’re supported by top-tier VCs and industry luminaries from Amazon, Google, Salesforce, Microsoft, and VMware.
1 note
·
View note
Text
Introduction
The DevOps approach has revolutionized the way software development and operations teams collaborate, significantly improving efficiency and accelerating the delivery of high-quality software. Understanding the DevOps roadmap is crucial for organizations looking to implement or enhance their DevOps practices. This roadmap outlines the key stages, skills, and tools necessary for a successful DevOps transformation.
Stage 1: Foundation
1.1 Understanding DevOps Principles: Before diving into tools and practices, it's essential to grasp the core principles of DevOps. This includes a focus on collaboration, automation, continuous improvement, and customer-centricity.
1.2 Setting Up a Collaborative Culture: DevOps thrives on a culture of collaboration between development and operations teams. Foster open communication, shared goals, and mutual respect.
Stage 2: Toolchain Setup
2.1 Version Control Systems (VCS): Implement a robust VCS like Git to manage code versions and facilitate collaboration.
2.2 Continuous Integration (CI): Set up CI pipelines using tools like Jenkins, GitLab CI, or Travis CI to automate code integration and early detection of issues.
2.3 Continuous Delivery (CD): Implement CD practices to automate the deployment of applications. Tools like Jenkins, CircleCI, or Spinnaker can help achieve seamless delivery.
2.4 Infrastructure as Code (IaC): Adopt IaC tools like Terraform or Ansible to manage infrastructure through code, ensuring consistency and scalability.
Stage 3: Automation and Testing
3.1 Test Automation: Incorporate automated testing into your CI/CD pipelines. Use tools like Selenium, JUnit, or pytest to ensure that code changes do not introduce new bugs.
3.2 Configuration Management: Use configuration management tools like Chef, Puppet, or Ansible to automate the configuration of your infrastructure and applications.
3.3 Monitoring and Logging: Implement monitoring and logging solutions like Prometheus, Grafana, ELK Stack, or Splunk to gain insights into application performance and troubleshoot issues proactively.
Stage 4: Advanced Practices
4.1 Continuous Feedback: Establish feedback loops using tools like New Relic or Nagios to collect user feedback and performance data, enabling continuous improvement.
4.2 Security Integration (DevSecOps): Integrate security practices into your DevOps pipeline using tools like Snyk, Aqua Security, or HashiCorp Vault to ensure your applications are secure by design.
4.3 Scaling and Optimization: Continuously optimize your DevOps processes and tools to handle increased workloads and enhance performance. Implement container orchestration using Kubernetes or Docker Swarm for better scalability.
Stage 5: Maturity
5.1 DevOps Metrics: Track key performance indicators (KPIs) such as deployment frequency, lead time for changes, mean time to recovery (MTTR), and change failure rate to measure the effectiveness of your DevOps practices.
5.2 Continuous Learning and Improvement: Encourage a culture of continuous learning and improvement. Stay updated with the latest DevOps trends and best practices by participating in conferences, webinars, and training sessions.
5.3 DevOps as a Service: Consider offering DevOps as a service to other teams within your organization or to external clients. This can help standardize practices and further refine your DevOps capabilities.
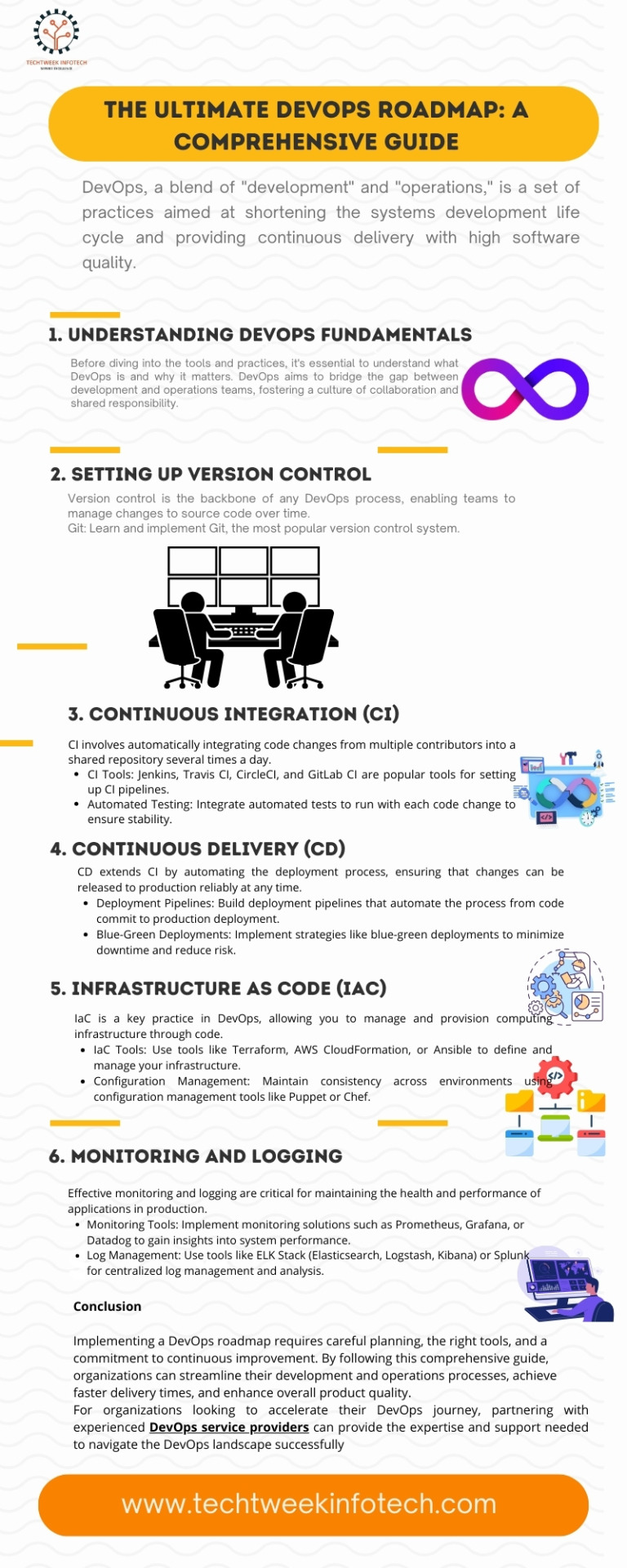
Conclusion
Implementing a DevOps roadmap requires careful planning, the right tools, and a commitment to continuous improvement. By following this comprehensive guide, organizations can streamline their development and operations processes, achieve faster delivery times, and enhance overall product quality.
For organizations looking to accelerate their DevOps journey, partnering with experienced DevOps service providers can provide the expertise and support needed to successfully navigate the DevOps landscape.
1 note
·
View note
Text
Container Monitoring Market Significant Players, Trends in Future, Revenue, Types, Scope Forecast 2031
The “Container Monitoring Market Share, Size, and Trends | 2031” is market research by The Insight Partners. The Container Monitoring market has perceived tides of change in the recent past. This study offers precise projections after detailed scrutiny of a range of factors impacting the business. Considering the present market scenario, this report brings forward correct predictions on revenue, market size, and CAGR of the Container Monitoring market. The novel market research which is based on a fact-based foundation is now accessible for purchase. This report can make a variance in wide decision-making and drive business forward in the right direction.
Business is no longer a game of instincts when it comes to capitalizing on new production lines. In a highly competitive Container Monitoring market, companies may face several challenges. Having trusted market research is always endorsed for both veteran and new entrants. Container Monitoring Market report presents a thorough analysis of local, regional, and global market scenarios through the following details.
Report Attributes
Details
Segmental Coverage
Component
Solution
Services
Deployment
Cloud
On-Premise
Industry Vertical
BFSI
IT and Telecom
Manufacturing
Retail and E-commerce
Transportation and Logistics
Government
Others
Geography
Regional and Country Coverage
North America (US, Canada, Mexico)
Europe (UK, Germany, France, Russia, Italy, Rest of Europe)
Asia Pacific (China, India, Japan, Australia, Rest of APAC)
South / South & Central America (Brazil, Argentina, Rest of South/South & Central America)
Middle East & Africa (South Africa, Saudi Arabia, UAE, Rest of MEA)
Market Leaders and Key Company Profiles
AppDynamics LLC (Cisco)
BMC Software, Inc.
Broadcom Inc.
Datadog, Inc.
Dynatrace LLC
New Relic, Inc.
Splunk Inc.
StackRox, Inc.
Sysdig, Inc.
VMware, Inc.
Other key companies
Competitive Landscape
Knowing the state of rivals is a strategically right move to outperform them. This report is the right place to explore key strategies, developments, and recent launches by key Container Monitoring market players. This report emphasizes an analysis of business strategies and expected growth opportunities for brands.
Key Coverings:
Current and Future Market Estimates- Container Monitoring Market Share, CAGR, and Forecast | 2031
Market Dynamics – Drivers, Challenges, Regional Trends, and Market Opportunities
Market Segmentation – Product, Application, End-use Industries, and Regional Growth Prospects.
Competition Matrix – Key Market Players and Strategies
Recent Developments and Innovation Contributing Market Growth
Need a Customized Market Research Report?
You can always share any specific requirements that you have, and our team will adjust the scope of research offerings as per your needs.
The following are some customizations our clients frequently ask for:
The Container Monitoring market report can be customized based on specific regions/countries as per the intention of the business
The report production was facilitated as per the need and following the expected time frame
Insights and chapters tailored as per your requirements.
Depending on the preferences we may also accommodate changes in the current scope.
Key Questions Addressed in the Container Monitoring Market Research Include:
What are present Container Monitoring market values, and what can be expected in the upcoming decade?
What are the key segments in the Container Monitoring market?
What is the regional distribution of the Container Monitoring market report?
What are the key players and their recent strategies?
What are the key factors driving Container Monitoring market growth?
What are regulatory concerns and requirements businesses have to compel?
Author’s Bio:
Anna Green
Research Associate at The Insight Partners
0 notes
Text
Precision Aquaculture Market Focus on Opportunities, Development Strategy, Future Plans, Competitive Landscape and Trends by Forecast 2031
The Insight Partners report, titled " Process Analytics Market Share, Size and Trends Analysis| 2031" provides investors with a roadmap for setting up new investment plans in the Process Analytics market. The report covers various aspects, ranging from a broad Process Analytics market forecast to intricate details like Process Analytics market size, both current and projected, market drivers, restraints, opportunities, and trends (DROT).
The Process Analytics market report also provides in-depth insights into major industry players and their strategies because we understand how important it is to remain ahead of the curve. Companies may utilize the objective insights provided by this market research to identify their strengths and limitations. Companies that can capitalize on the fresh perspective gained from competition analysis are more likely to have an edge in moving forward.
With this comprehensive research roadmap, entrepreneurs and stakeholders can make informed decisions and venture into a successful business. The key companies identified in the Process Analytics market analysis by our research analysts are Alpine Data Labs, .IBM Corporation, Microsoft Corporation, MicroStrategy Incorporated, Oracle Corporation, SAP SE, SAS Institute, Splunk Inc, Tableau Software Inc, Verint Systems Inc. . This research further reveals strategies to help companies grow in the Process Analytics market.
A market research report, which contains proof of market research and provides the best opportunity for businesses to fulfill their objectives, might serve as the cornerstone of your business strategy. Insights on all significant regions and associations are included in this study, which also provides information on subsegments. This report delves even further into the challenges faced by Process Analytics market enterprises in terms of cost and return on investment, as well as Process Analytics market trends.
What are the Main Focal Points Covered in this Report?
1. Process Analytics Market Outlook - Various factors that determine Process Analytics market growth are examined in this section, including opportunities, barriers, challenges, trends, and drivers. Authentic market determinants encourage innovation. This section addresses the distribution of firm activity and the factors that influence development. A comprehensive range of market-specific data is available, allowing investors to conduct an early assessment of the Process Analytics market's capabilities.
2. Competitive Comparison Matrix- The purpose of this segment in the Process Analytics market report is to present organizations with a competitive comparison matrix. This section provides an in-depth assessment of competitors' business strategies and advancements. Businesses can employ detailed market research and target statistics to determine competitors' alternatives. Businesses might discover new market niches and avenues for sales by examining their competitors' offerings.
3. High ROI Trade-Offs- To adequately aid their customers in a competitive Process Analytics market, enterprises must educate themselves on key domains. Streamlining market approaches is an effective application of market research. This study area focuses on product, application, and regional categories. Understanding demographics and high-ROI geographical regions helps entrepreneurs optimize their products.
Perks for Buyers
Strategic Insights to Enhance Customer Experience and Per Customer Revenue
Assistance in Product Planning and Roadmap to Marketing
Data-backed Approach by Researchers to Offer New Optimal Business Solutions.
Preferred Target Demographic, Target Regions, and Market Channels.
Get Customized Insights and Consultation ServiceOn the Basis of Component this market is categorized further into-
Solution
Services
On the Basis of Deployment this market is categorized further into-
On-Premise
Cloud
On the Basis of Organization this market is categorized further into-
Large Enterprises
Small and Medium Enterprises
On the Basis of Application this market is categorized further into-
Business Process
Information Technology Process
Customer Interaction
Key regions Process Analytics Market Research Report:
North America (U.S., Canada, Mexico)
Europe (U.K., France, Germany, Spain, Italy, Central & Eastern Europe, CIS)
Asia Pacific (China, Japan, South Korea, ASEAN, India, Rest of Asia Pacific)
Latin America (Brazil, Rest of Latin America)
The Middle East and Africa (Turkey, GCC, Rest of the Middle East and Africa)
Rest of the World
Author’s Bio:
Shashikant Ligade
Senior Analyst The Insight Partners
1 note
·
View note
Text
AVA EDUCATION

AVA Orange publications are the latest tech knowledge books for higher academics. We are more than just a place for books, we’re a community of learners, tech enthusiasts, and innovators who share a passion for staying up-to-date with the latest in technology.
At Orange AVA, we are dedicated to providing a comprehensive suite of services that propel businesses into the future. Our core offerings include: 1) Cutting-edge Publishing Services: If you are someone who has a passion to communicate ideas and would like to reach masses in the technology world then we offer the best editorial services to help you get published as an idea propagator and skilled trainer in any technical domain. Your dream to become an author is realised with us.
2) Training and workshops: Through our immersive training and workshops we empower individuals and teams with the skills and knowledge necessary to navigate the rapidly evolving tech landscape. Furthermore, our commitment to fostering innovation extends to product development, where we collaborate with clients to transform visionary ideas into reality, delivering solutions that redefine industries.
3) Technical Hiring Solutions: We are not just a service provider; we are your strategic partner. Leveraging our extensive network and expertise, we connect businesses with top-tier tech professionals, ensuring the right talent for your specific requirements. Additionally, our dedication to continuous learning is evident in our tech learning and development initiatives, designed to keep your workforce adaptive and proficient in the latest technologies.
Join us on the journey to success, where Orange AVA transforms possibilities into realities, one innovative solution at a time.
Day-by-day our digital network is spreading all over the country giving students free access to the company website: www.orangeava.com
As a part of Orange Education Pvt Ltd, AVA was created with a clear goal — to help individuals gain the newest insights and skills in every technical domain for career and business success. Our best-selling books, like Modern Web Development with Go, Ultimate Neural Network Programming with Python, Ultimate Salesforce LWC Developers’ Handbook, and Ultimate Splunk for Cybersecurity, symbolises this commitment by providing practical knowledge for real-world applications. Our team includes tech experts, experienced authors, and dedicated professionals, all working together for excellence in the world of Technology and its applications.
0 notes
Text
Virtusa Acquires BRIGHT, Deepening ServiceNow and Splunk capabilities for Enterprises
Virtusa Acquires BRIGHT, Deepening ServiceNow and Splunk capabilities for Enterprises Acquisition expands Virtusa's offerings with solutions-based approach for customers
Acquisition expands Virtusa’s offerings with solutions-based approach for customers Virtusa Corporation, a global provider of digital strategy, digital engineering, and information technology (IT) services, announced an expansion to its business solutions portfolio through the acquisition of BRIGHT, one of the largest elite partners to ServiceNow & Splunk in EMEA. This acquisition will enable…

View On WordPress
0 notes
Text
Splunk partners with Microsoft to strengthen digital resilience
http://i.securitythinkingcap.com/SsM3j6
0 notes
Text
Data Engineering Courses – Equipping Your Team with the Skills to Flourish
The world today is highly data-driven. To stay relevant in this technological realm and enjoy continued growth, IT teams need to master data engineering skills. Data engineering courses offer incredible opportunities to learn how to design, implement, and manage data infrastructure and pipelines across diverse industries.
Let us now explore some of the most popular data engineering courses and how these courses equip teams to grow.
Data Engineering with Python Training Course – To Shine as A Data Analyst
The data engineering with Python training course has been designed to offer the fundamental skills required to create, process, and evaluate data using the Python programming language.
During the course, learners will be introduced to manipulation libraries, data visualization tools, and data processing techniques. If you are keen to excel as a Data Analyst, Python Developer, or Data Engineer in e-commerce, finance, or healthcare industries, this is the best data engineering course out there.
Operational Data Analytics - To Explore IT Operations Engineer Roles
This will be an ideal course for IT Operations Engineers, Data Analysts, or Security Analysts. The operational data analytics with Splunk Training course is currently one of the best courses in this field.
Such data engineering courses focus on operational data analytics, acquiring insights into data, and monitoring operational performance. As learners progress through the course, they will learn how to process and visualize data to ensure accurate monitoring and troubleshooting.
Excel In Managerial Roles with Data Engineering for Managers Training
The course has been designed to equip managers and leaders with the skills to monitor data engineering initiatives in their respective organizations.
Through such data engineering courses, managers learn about best practices for managing data engineering projects, fundamentals of data architecture, and ideal governance practices for data architecture. Once you have been certified, you will be capable enough to lead data engineering teams, excel in strategic decision-making, and enjoy successful project results.
Final word
Data engineering courses offer excellent options for teams looking for ways to enhance their skills in the highly competitive data-driven realm. Whether you need to master Python to tackle data manipulation or utilize Splunk to manage operational analytics, these courses will equip your team with knowledge and updated skills to excel across diverse industries.
From health care and finance to cyber security and e-commerce, Data Engineers now have a crucial role in ensuring efficiency, innovation, and productivity in organizations across different industries worldwide. A deep understanding of data engineering skills and experience gained through practical sessions will position your team for continued advancement.
Partner with a reliable and reputed course provider like Web Age Solutions to ensure you receive accredited and recognized certifications that will prepare your team for unprecedented growth.
For more information visit: https://www.webagesolutions.com/courses/data-engineering-training
0 notes
Text
Trainocate: A Leading Learning & Development Service Provider can help advance IT careers
Trainocate: A Leading Learning & Development Service Provider can help advance IT careers
BANGALORE, India, May 23, 2022 /PRNewswire/ — Trainocate is one of the most established IT and human capability development training providers in the world, partnering with over 30 plus vendors and 1500 plus corporate clients. Trainocate dominates the market with a strong presence in the Asia-Pacific region, operating in 19 locations across 14 countries. In 2021 Trainocate trained and certified…

View On WordPress
#amazon#American Management Association#APJC#Asia-Pacific#AWS Discovery Day#Big data analytics#Cisco Learning#india#Learning Partner of Year 2019#Microsoft#Microsoft Worldwide Learning Partner#PWR PWR#Splunk •#Training Industry#UiPath
0 notes